
Cybersecurity in Healthcare: vulnerabilities, trends and challenges
- Posted In:
- Vigilància tecnològica
- Maria Garrido
- no comments
Over the last years, hospitals and health systems have increasingly embraced digital technologies, such as cloud, Big Data, Internet of Things (IoT), remote monitoring, and more, to offer the best patient care. However, as more digital technologies are adopted, the risk of cyberattack potentially increases.
Healthcare data is particularly sensitive to cyberattack, since healthcare cyber breaches often involve loss of sensitive personal information and medical records. Digitally-connected medical devices are also susceptible to cyberattack, and interference with how these devices operate could potentially lead to patient harm or even death.
In addition to this, the emergence of Covid-19 has boosted the digitalisation process of healthcare systems worldwide, increasing the associated cybersecurity risks. To cope with the pandemic, health systems have performed several actions to care for an unprecedented number of patients, but some of these actions have led to a breach in cybersecurity:
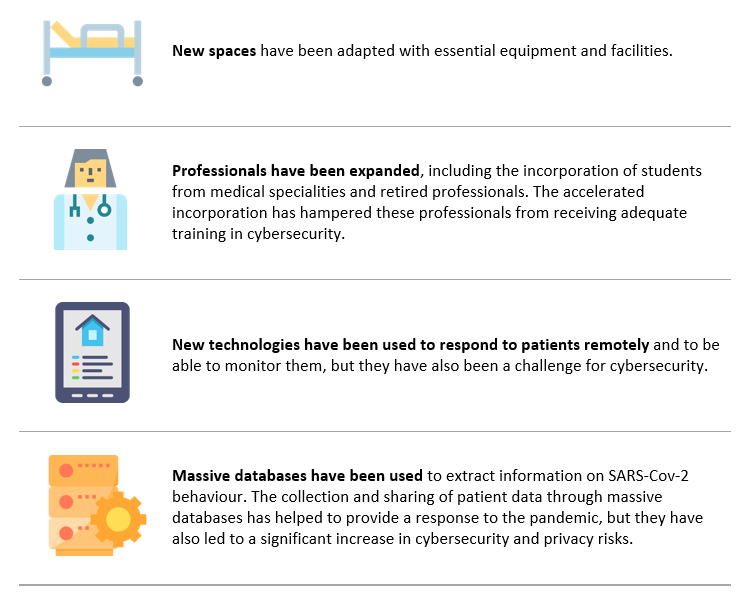
In this scenario, healthcare systems are actually plagued by cyberattacks that are advanced, persistent, and which can wreck both operations and reputation. Healthcare organizations manage an array of assets, including infrastructure, applications, managed and unmanaged endpoints, mobile devices, and cloud services, all of which can be attacked. Given the increasingly sophisticated and widespread nature of these attacks, the healthcare industry must make cybersecurity a priority and commit to the investments necessary to protect its patients.
Cyber-attacks on independent practitioners as well as large, integrated healthcare systems have infected even the most protected networks. In 2021, healthcare systems suffered the highest number of cyber-attacks, with ransomware -1.203 attacks of this type where reported-, and phishing attacks as the leading dangers, some of them affecting a large number of patients. In the same year, 45.67 million patient records were breached, confirming the highest levels of exposure since 2015.
Here, the top 4 cybersecurity threats and vulnerabilities that affect the healthcare systems are summarised:
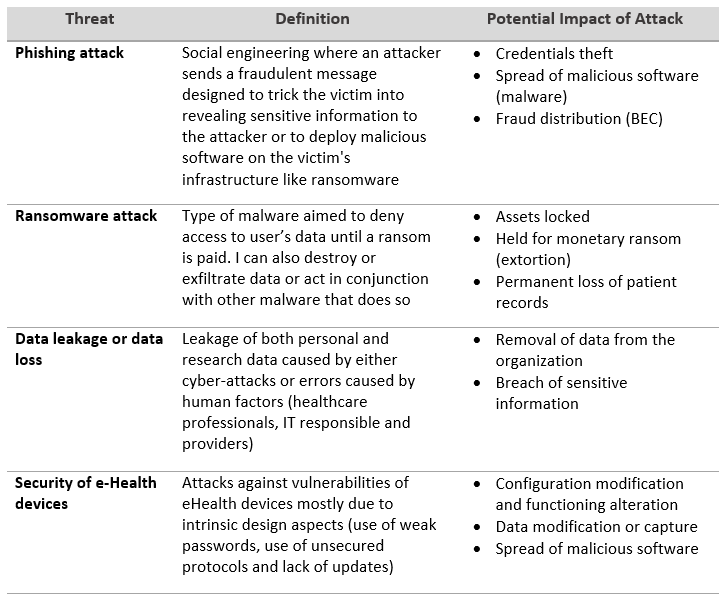
In the following 4 sections, these type of threats are studied in more detail.
What is phishing and its motivations
Phishing is a fraudulent practice that consists of simulating a false identity, often by impersonation of the identity of a person or a specific organization, with the aim of inciting victims (contacted by e-mail, telephone or text message) to carry out an action that would enable cybercriminals to steal their personal data, usually data credentials or credit card numbers.
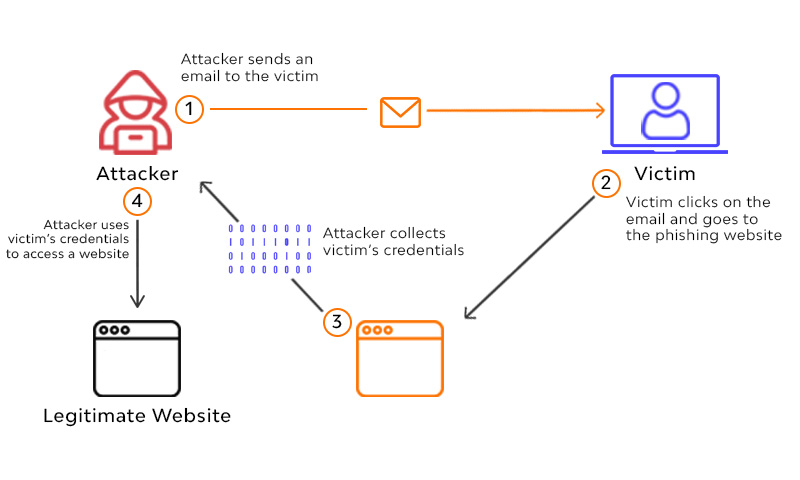
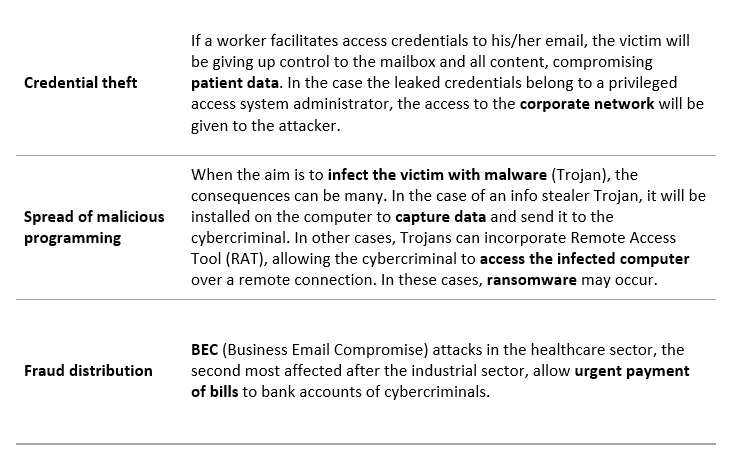
This type of attack is usually used by cybercriminals in credential theft, the spread of malicious programming and also fraud distribution:
Must-Know phishing statistics in Healthcare
- 60% of phishing cases are aimed at access credentials and contain a link to a fraudulent website
- One in four health professionals opens a phishing email; one in six clicks on the malicious link and, approximately 7% of them give information
- Phishing has become the main method of attack against the healthcare sector; in Spain, it represents 57% of cyber-attacks against this sector
What is Ransomware and how it works
Ransomware is a type of malicious software (malware) that threatens to block access to data or a computer system, usually by encrypting it, until the victim pays a ransom fee to the attacker. Hackers also may deploy ransomware that destroys or exfiltrates data, or ransomware in conjunction with other malware that does so.
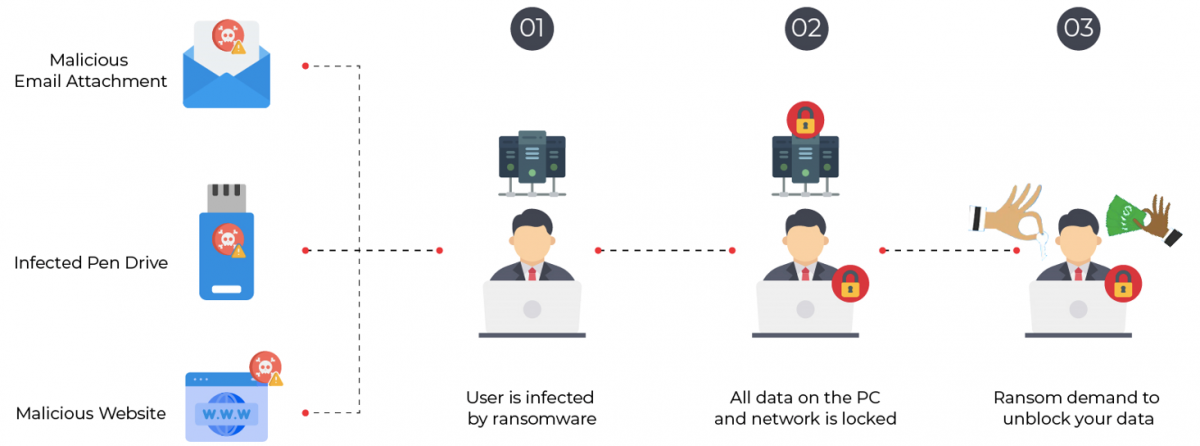
A ransomware incident in a healthcare system can lead to serious consequences:
- Patients’ health impact. The disruption of healthcare services can put patients’ lives at risk.
- Economic impact. Economic losses caused on the affected systems can be at least 760.000 €, assuming that no ransom is paid. It may also require penalties arising from non-compliance with cybersecurity regulations.
Must-Know ransomware statistics in Healthcare
- Malware distributed via phishing is the second most common way for ransomware to enter the healthsector, representing the 26.3% of the ransomware attacks
- The number of ransomware attacks against hospitals increased by 60% in march 2020
- In Spain increased by 160%; in Germany 145%; in UK 80% and in France 36% the same year
In the healthcare sector, personal and research data leakage have their origin in cyber-attacks, motivated by the high value of these, and errors caused by the human factor. The diversity of entities in this sector, the volume of digitised data and the high connectivity are some of the reasons why the risk of data leakage is increasing.
Data of interest
Data theft represents an opportunity for cybercriminals as they can be easily monetised. These data can be:

Medical data
Personal data, medical records, health records, laboratory test results, diagnoses, medical invoices, insurance data, bank accounts, insurance, x-rays, etc.
These data are sold on the dark web, where they are bought at high prices -a complete health profile can be worth between 200 – 830 €- to perpetrate crimes of identity theft, financial fraud or extortion.

Research data
Research information, intellectual property or drug test results. This information has great economic value and is the result of years of expensive research and experiments.
Types of errors
Information leaks originate from unauthorised accesses -22% of reported cases-, which can occur for two reasons:
- Errors caused by the human factor. These errors are common among health professionals and are essentially a symptom of a lack of awareness. This results in bad practices such as the processing of patients’ medical data outside the central information systems and without encrypting, with the risk to end up in the wrong hands.
- Intentional actions perpetrated by internal employees -called internal threat-. In this case, the employee tries to steal information through external storage devices, makes a copy of on the cloud or sends it to a private email account. The reasons why an employee decides to act against his own organisation can be economic -sale of data- or revenge.
Some data leakage statistics in Healthcare
- In 2020, the number of information leakage reported to the authorities was 25% higher than in 2019, and 100% higher than in 2014.
The pandemic has boosted e-Health technologies for telemedicine, unified information management and efficient disease control. These include Internet of Health Things (IoHT) and m-Health:
- IoHT. Medical control devices installed in hospital beds with network connectivity (respirators, arterial control, blood oxygen level, blood pressure, anti-coagulants, etc.). These devices allow an intelligent approach to the service and more accurate and efficient decision-making. Data generated by this medical equipment is combined with other safety-related data and integrated, in real time, into a central control system.
- m-Health. Mobile devices that provide Health services. These devices allow real-time and remote monitoring, as well as tracking of the disease.
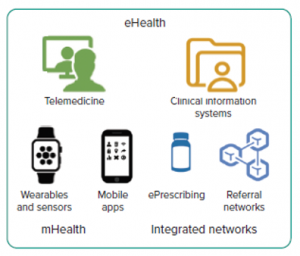
Vulnerabilities of e-Health devices
The most common vulnerabilities are due to aspects intrinsic to their design, such as the use of weak passwords, the use of unsecured protocols, as well as the lack of updates.
- IoHT. Difficult to keep them updated due to their variety -8% of the devices connected to medical centres-. After 10 years, the more expensive ones -diagnostic devices, laboratory tests or medical imaging- can be considered obsolete because they do not receive the relevant updates.
- m-Health. Development and publication of Covid-19 tracking apps in a record time has meant that they have not been adequately evaluated from a cybersecurity point of view.
It is crucial to segment the network -see Cybersecurity trends in Healthcare section- so that potentially vulnerable devices cannot interfere in the parts of the network where there are more critical elements.
Which are the consequences?
The vulnerabilities mentioned above can lead to serious consequences:
- Affecting the privacy of patients’ data
- Degrading the quality of treatment
- Being exploited to carry out a cyber-attack -control gain, configuration modification, data capture, malware deployment-
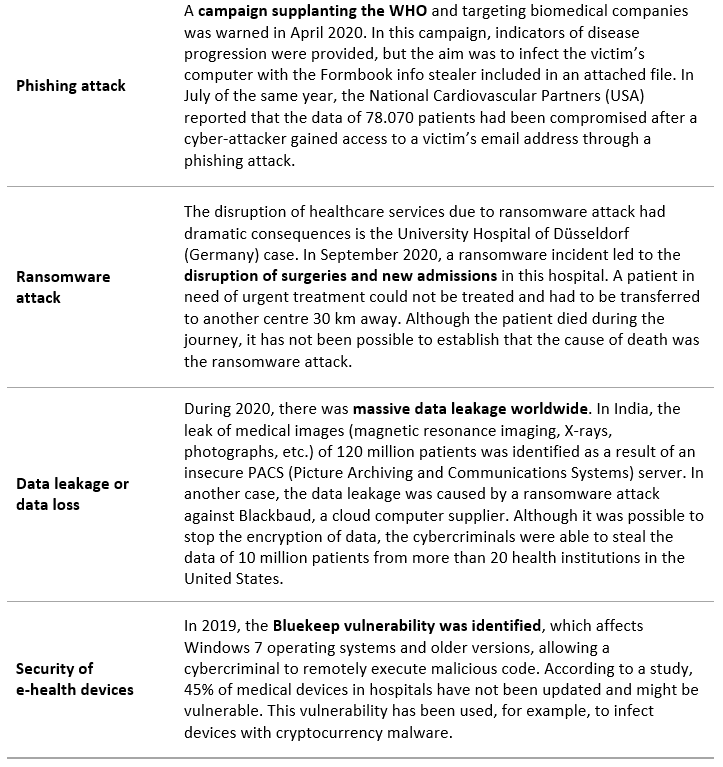
The following examples of cybersecurity breaches exemplify the variety of attacks the healthcare field has faced worldwide, and the consequences of these attacks for organizations:
To protect the network and data of healthcare systems, and any other organisation, it is important to understand the different types of cybersecurity and how they defend against cyber threats.
The different cybersecurity solutions in the market serve the same purpose: to ensure the confidentiality, integrity, and availability of data and to protect the cyber assets.

Network security
Activities and controls designed to protect the integrity of the networking infrastructure, defending the network and the data against threats, unauthorized access, intrusions, breaches, misuse and so forth.
Network security ensures that the entire underlying network infraestructure, from devices and applications to end-users, is working securely. A large variety of technologies and tools can be found on the market, such as firewalls, intrusion detection/protection systems –IDS and IPS– and virtual private networks (VPNs).

Endpoint security
Considered as a subset of network security, the endpoints that need to be secured include:
- Desktops and laptops
- Mobile devices -smartphones and tablets-
- Network devices -modems and switches-
- Connected or Internet of Things (IoT) devices -including connected printers, smart assistants, and sensors-
Common types of endpoint security solutions and best practices include: 1) endpoint protection platforms (EPP) and endpoint detection and response (EDR); 2) disk encryption, and 3) mobile device management (MDM).

Cloud security
It refers to the technology, policies, and processes used to mitigate the security risks of cloud computing (public, private, or hybrid clouds).
In general, the provider is responsible for the security “of” the cloud (underlying infrastructure) and the cloud consumer (the organization) is responsible for the security “in” the cloud (data and management).
Solutions to consider for securing the cloud are: 1) cloud access security broker (CASB); 2) identity and access management (IAM), and 3) multifactor authentication.

Application security
Although being a major focus for developers, it goes beyond the development and design process. Organizations need to continuously ensure that applications they have deployed remain secure throughout their lifecycle.
These are some of the practices and solutions to consider for this type of cybersecurity: 1) SaaS management; 2) risk assessment and patching, and 3) access controls.

Internet security
Internet-borne threats are behind the majority of data breaches. Although other types of cybersecurity help defend against internet threats, the prevalence and magnitude of these threats warrant placing internet security into its own category.
To protect organizations against internet threats, some of the cybersecurity measures to consider include: 1) DNS-layer protection; 2) email security, and 3) URL filtering.
In 2022, cyber-threats against the healthcare industry will likely continue. To be secure, medical device manufacturers and healthcare providers will need to go beyond defensive cybersecurity strategies and incorporate cyber resiliency.
As more healthcare organizations are aware of the importance of implementing tools and strategies in terms of cybersecurity, the following cybersecurity trends are expected to emerge.
Trend 1: Prevention begins with endpoint education
- Employees are on the front line of defense against cyberattacks, since endpoint security systems can fail to capture all threats. This means that cyber risk education is vital.
- Since endpoints are the weakest link in a clinical setting, healthcare organizations would benefit of having rigorous and effective endpoint security measures.
- All healthcare organizations should seek ongoing training programmes for data privacy, protection, and cybersecurity, and aimed to different categories of staff (IT-personnel, medical personnel, and decision-makers).
Trend 2: Multi-factor authentication uptake is on the rise
- Multi-factor authentication adds a layer of security for the environment, and it is widely valued in healthcare settings and its adoption continues to rise.
- By working with security providers, healthcare organizations can facilitate the implementation of two-factor authentication at a low cost as well as its integration with internal systems.
- Enabling two-factor authentication has become key for healthcare providers as they look to protect patient data from unauthorized access and tampering.
Trend 3: Biometrics
- Biometrics allows to identify and authenticate individuals in a fast and reliable way, through the use of unique biological characteristics. This technology is being explored by more advanced healthcare organizations.
- It is expected that the use of biometrics in healthcare organizations will grow over the next three to five years, as a way to offer extra cybersecurity layers, control identity management and access.
- The main barrier to implementing biometric measures for patients remains privacy and security. Thus, biometric measures are currently limited to clinical staff.
Trend 4: Network segmentation reinforces providers' security
- Network segmentation involves separating each network and making it visible only to those who have the right to access it. It represents a way to control levels of access to sensitive data.
- It can limit access to medical data and ensure compliance with regulations.
- Moreover, network segmentation can help restrict the movement of the threat across the networks.
Trend 5: Real-time analytics detect advanced threats
- While healthcare providers already apply analytics to some extent to improve population health management and clinical efficiency, it has not yet been used to reinforce the security position of companies and organizations.
- Behavioral analysis is a niche technique within the healthcare sector; in other industries, it has already proven to be effective against outsider and insider threats by detecting abnormal activities.
- Real-time analytics are considered more powerful, as legacy security information and event management Systems are no longer well-placed to detect advanced threats.
Trend 6: Push for increasing medical device cybersecurity regulations
- Novel medical devices are increasing in connectedness to the Internet, and can receive data, send data, or both. The use of these connected devices brings the risk for hacking directly to patients.
- The EU has recently initiated the GDPR and published cybersecurity recommendations for medical device industry. Similarly, the FDA has issued two guidance documents for medical device manufacturers.
- More stringent regulations and guidelines are crucial to encourage manufacturers to incorporate cybersecurity as a core component of device development.
EU measures
The NIS2 Directive
The Network and Information Security (NIS) Directive is the first piece of EU-wide legislation on cybersecurity, and its specific aim was to achieve a high common level of cybersecurity across the Member States. While it increased the Member States’ cybersecurity capabilities, its implementation proved difficult, resulting in fragmentation at different levels across the internal market.
To respond to the growing threats posed with digitalisation and the surge in cyber-attacks, the Commission has submitted the NIS2 to replace the NIS Directive and thereby strengthen the security requirements, address the security of supply chains, streamline reporting obligations, and introduce more stringent supervisory measures and stricter enforcement requirements, including harmonised sanctions across the EU.
Medical Device Regulation 745/2017 (MDR) and In Vitro Diagnostic Regulation 746/2017 (IVDR)
Approved on May 25 2017, MDR and IVDR establish relevant guidelines in relation to medical devices incorporating information systems. They place cybersecurity as an aspect to be taken into account throughout the entire lifecycle of devices, from the design and manufacturing processes to their withdrawal.
Thus, manufacturers are responsible for developing and manufacturing medical devices in accordance with the state of the art, the principles of risk management and best practices in cybersecurity. Health centres must adapt their processes to comply with these best practices. The two regulations also establish the obligation to obtain a certificate (CE marking) and follow the cybersecurity requirements to be able to supply devices to member states.
General Data Protection Regulation (GDPR)
Approved by the European Parliament on April 14 2016, it came into effect on May 25 2018. GDPR sought to protect and empower EU citizen data privacy and enforce structural changes in the way that organizations approach customer data privacy and protection.
To align with GDPR regulations, health systems have had to make operational and technological advancements. Under GDPR, non-compliant organizations could suffer fines of 4% of their annual turnover or €20M ($26M).
National measures
Esquema Nacional de Seguridad (ENS)
The ENS establishes the principles that regulate and ensure the access, integrity, availability and truthfulness of the information used in electronic media in or related to Public Administrations (state, regional and local). The regulation has undergone constant evolution since its first development in 2010 (royal decree 3/2010, 951/2015 and 311/2022).
The ENS is the result of the work of Ministerio de la Presidencia and later of Ministerio de Política Territorial and Administración Pública, with the support of Centro Criptológico Nacional (CNN) and the participation of all Public Administrations.
Ley Orgánica de Protección de Datos Personales y garantía de los derechos digitales (LOPD-GDD)
Approved on October 18 2018, LOPD-GDD adapts Spanish law to the model established by GDPR. Its purpose is to protect the intimacy, privacy and integrity of the individual, in compliance with article 18.4 of the Spanish Constitution. In the same way, it regulates the obligations of the individual in all data transfer processes to guarantee the security of the exchange.
LOPD-GDD establishes many changes with respect to the previous Ley de Protección de datos (1999), modifying the requirements to obtain information, save it or share it, and establishes changes in relation to the treatment of user data on the Internet.
ISO/IEC 27000
ISO 27000 is a standard that defines how an Information Security Management System should be implemented in a company or organization.
Its implementation offers organizations (public and private) the advantage of protecting their information in the most reliable way, pursuing three main objectives: 1) preserve the confidentiality of the data; 2) preserve the integrity of the data, and 3) availability of protected information.
Healthcare systems face numerous threats from cyber-attacks as detailed above, and hospitals are spending huge money to prepare firewalls and protect their patients’ data.
The global healthcare cybersecurity market was valued at $12.85 billion in 2020, and is projected to reach $57.25 billion by 2030, growing at a CAGR of 16.3% during the forecast period.

Market drivers
Increased number of cyber-attacks and rise in demand for cloud services propel the growth of the global healthcare cyber security industry.
Moreover, regulatory and government policies encouraging improvement in the security standards of the healthcare industry positively impact the growth of the healthcare cyber security market growth.

Market by type of attack
The ransomware segment had the most substantial growth in the market in 2020. Increasing data breaches caused by using this software are attributed to this development.

Market by type of cybersecurity
The network security segment dominated the market share in 2020, and is expected to continue this trend.
However, the application security segment is expected to witness highest growth in the upcoming years, as the healthcare sector has inclined toward application security solutions to safeguard their data.
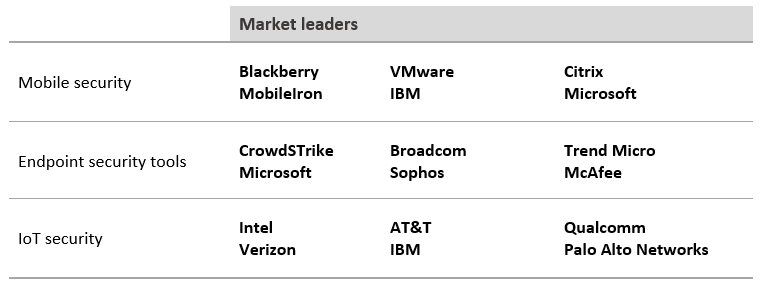
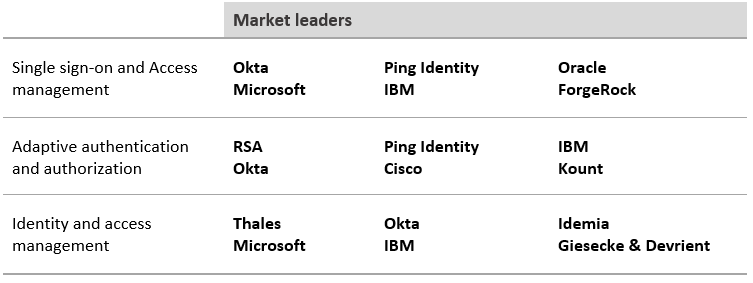
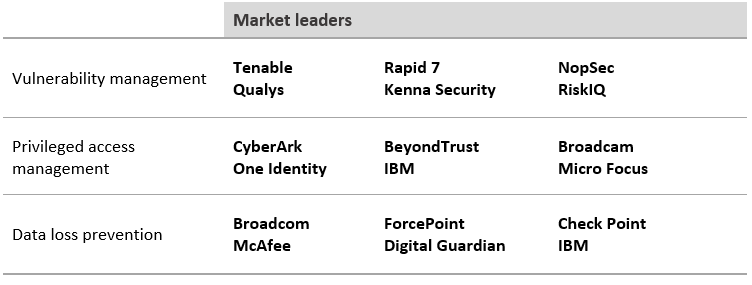
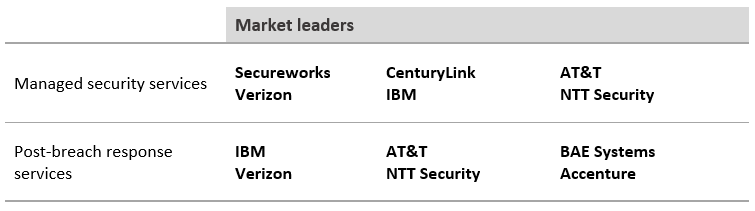
In this section, the major technology areas that make up the cybersecurity sector are detailed, as well as the leading players.
Security operations centers
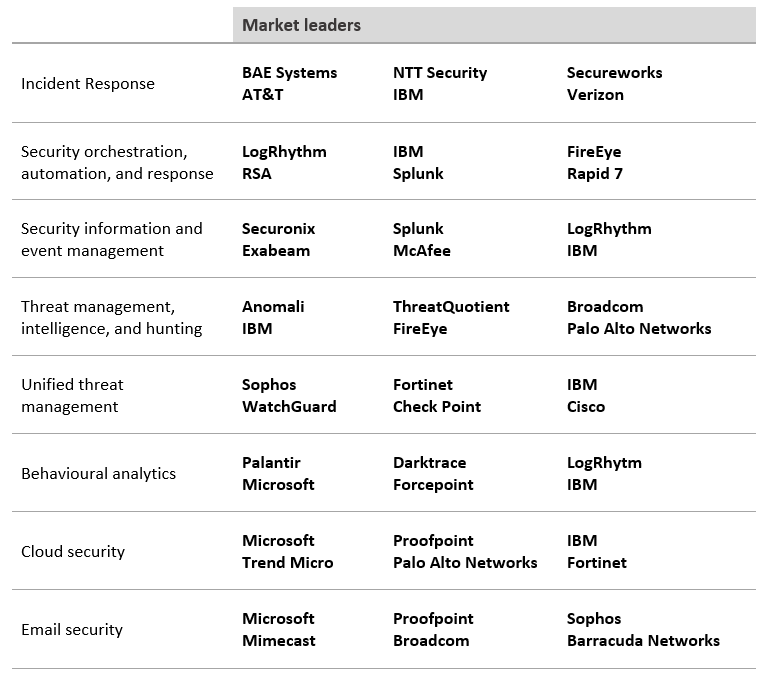
Security engineering
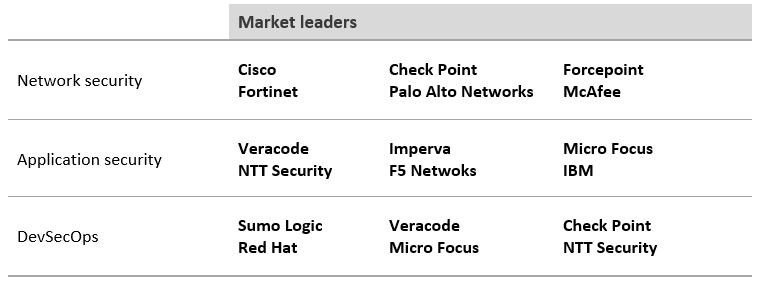
Device security
User and identity
Global risk and compliance
Security services
Maria Garrido
Llicenciada en Química (UAB) i doctorada en Química Orgànica (UB). Després de treballar durant molts anys com a investigadora en projectes de Química Mèdica, vaig tenir l’oportunitat d’endinsar-me en el món de la innovació en el sector de la salut. A l’I3PT treballo a la Unitat d’Innovació com a gestora de projectes d’innovació sanitària.
All stories by: Maria Garrido



Leave a Reply